The healthcare industry is increasingly reliant on software to deliver efficient patient care, making HIPAA compliance an essential journey for healthcare software developers. This journey isn’t a single step but a continuous path of adherence to regulations designed to protect patient privacy and data security.
Embarking on this journey requires a methodical approach, starting from the earliest planning stages to post-deployment and beyond. Here we outline the critical steps and strategies to navigate the complexities of HIPAA compliance, ensuring that patient data is safeguarded throughout the lifecycle of healthcare software.
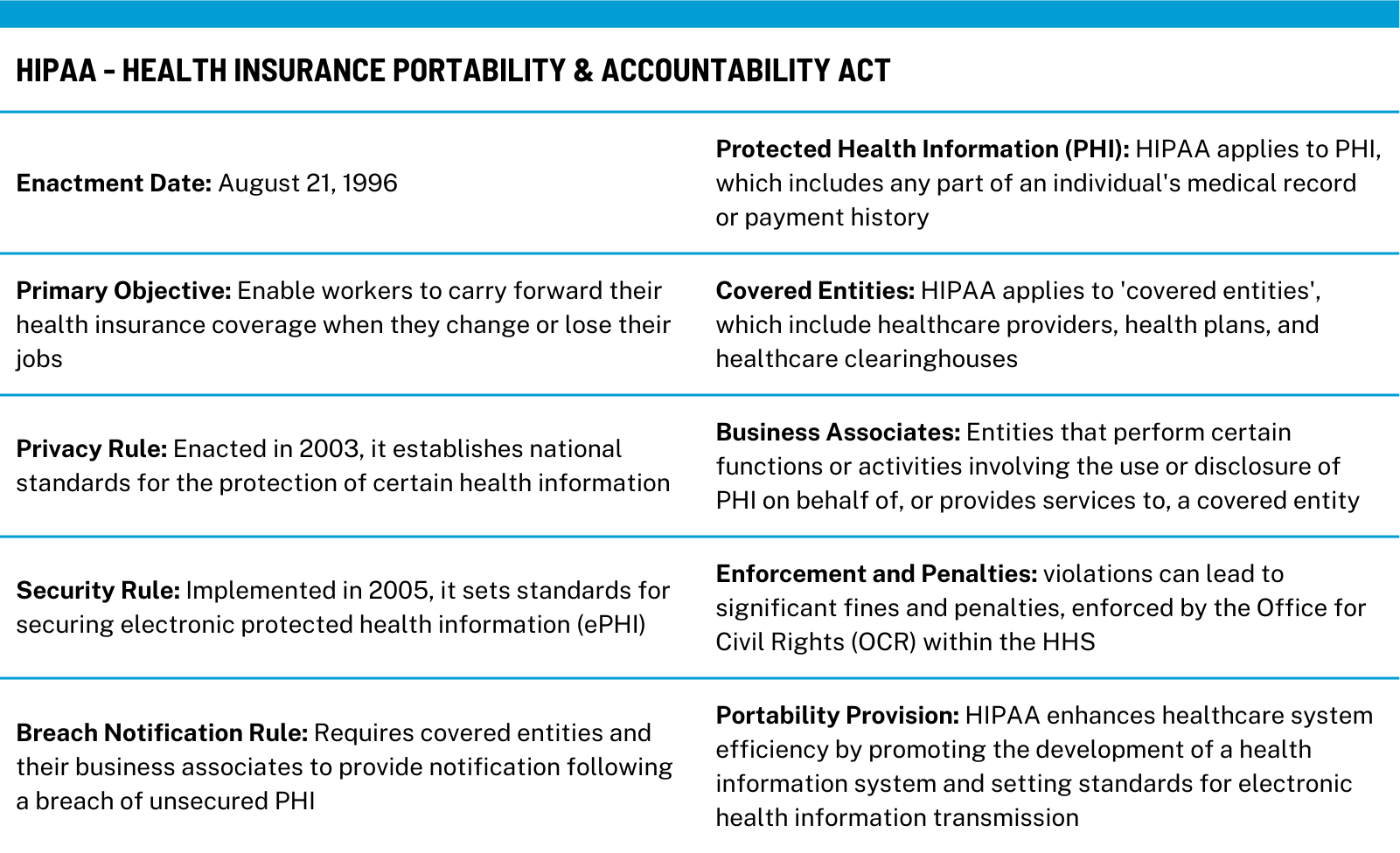
Understanding the Basics of HIPAA
While the Health Insurance Portability and Accountability Act (HIPAA) has been a cornerstone of patient data protection since 1996, its principles are especially pertinent in today’s digital age. Before diving into the development of healthcare software, it’s crucial to grasp HIPAA’s key tenets: the Privacy Rule, the Security Rule, and the Breach Notification Rule.
These form the framework for the protection of Protected Health Information (PHI), which is any information in a medical record that can be used to identify an individual. Even as we delve into the practical steps towards compliance, keeping the fundamentals in mind ensures a strong foundation for the journey ahead.
Pre-Development: Planning and Assessment
The compliance journey begins long before a single line of code is written. Initial planning must involve a comprehensive risk assessment to identify where PHI will be stored, processed, and transmitted by the software. This phase should address the following:
- Data Flow Analysis: Map out the journey of PHI within your software, from input to storage to output.
- Threat Modeling: Identify potential security threats to PHI at each stage of data flow.
- Gap Analysis: Compare current security measures against HIPAA requirements to identify areas needing improvement.
This proactive assessment sets the stage for a development process that embeds HIPAA compliance into the very fabric of the software.
Development: Building with Compliance in Mind
Developing healthcare software with HIPAA compliance in mind is a meticulous process that requires a detailed approach. Here’s how developers can integrate compliance from the get-go:
- Privacy by Design: Adopt a privacy-centric approach during the product design phase. This means considering patient privacy in every feature and function of the software.
- Secure Development Lifecycle: Incorporate security checkpoints at each stage of the development lifecycle. This includes code reviews, vulnerability assessments, and penetration testing to identify and mitigate risks.
- Encryption Standards: Implement strong encryption standards for PHI, ensuring that all data, both at rest and in transit, is encrypted with state-of-the-art algorithms.
Testing and Validation
Testing for HIPAA compliance involves more than functional testing. It includes:
- Compliance Testing: Regularly test the software against compliance benchmarks to ensure all features meet HIPAA standards.
- Audit Controls: Develop and test audit controls to record and examine access and other activity in systems that contain or use PHI.
- Third-Party Validation: Engage with external experts to conduct security assessments and validate compliance. This independent review can provide an objective analysis of the software’s security and compliance posture.
Post-Deployment: Monitoring and Management
After deployment, the journey to maintain the software and its HIPAA compliance continues with:
- Continuous Monitoring: Implement tools and processes to continuously monitor PHI access and system integrity.
- Update and Patch Management: Establish a protocol for the regular update and patching of the software to address new threats and vulnerabilities.
Incident Response Planning: Develop an incident response plan that outlines steps to be taken in case of a security breach, including how to notify affected parties and authorities as required by the Breach Notification Rule.
Training and Documentation
An often overlooked but vital aspect of HIPAA compliance is:
- Staff Training: Ensure that all team members are trained on HIPAA requirements and understand the importance of protecting PHI.
- Comprehensive Documentation: Maintain detailed documentation of all compliance-related policies, procedures, and actions. This serves as evidence of compliance efforts and a reference in case of audits.
Common Pitfalls to Avoid
The path to HIPAA compliance is fraught with potential missteps. Being aware of common pitfalls can help you navigate more smoothly:
- Underestimating the Scope of PHI: PHI can be broader than initially thought. Ensure all forms of PHI, including images and free-text fields, are identified and protected.
- Neglecting Employee Training: Compliance is not solely a technical issue. Human error can lead to breaches, making regular staff training essential.
- Overlooking Regular Risk Assessments: Threat landscapes change; so should your risk assessments. Conducting them regularly helps in identifying new vulnerabilities.
- Failing to Enforce Access Controls: Not limiting access to PHI on a need-to-know basis can lead to unnecessary exposure. Strict access controls are imperative.
Best Practices for Maintaining Compliance
Adhering to best practices is key to not only achieving but also maintaining HIPAA compliance:
- Stay Informed: Healthcare laws and technologies evolve. Stay informed about changes in HIPAA regulations and technology to ensure ongoing compliance.
- Implement a Culture of Compliance: Foster a workplace environment where compliance is a shared responsibility and an integral part of the corporate culture.
- Engage in Continuous Improvement: Use audits and incidents as learning opportunities to strengthen your security posture and compliance mechanisms.
- Data Minimization: Adopt the practice of collecting only the data that is necessary, reducing the risk of exposure.
The Takeaway
Achieving and maintaining HIPAA compliance is a dynamic and ongoing process that is crucial for the trust and safety of patients in the digital healthcare era. It demands a proactive approach, attention to detail, and a culture of continuous improvement.
If you’re in the process of developing healthcare software and looking to ensure HIPAA compliance, or if you need expert assistance in evaluating or enhancing your current systems, we are here to help. Our experience in delivering HIPAA-compliant solutions can guide you through the intricate process of safeguarding patient data. Reach out to us to learn more, access resources, or take the first step towards a partnership.